How to install snort intrusion detection system on Ubuntu!
Snort is a signature based intrusion detection system, it either drop or accept the packets coming on a certain interface depending on the rules you have used. In a signature based intrusion detection system packets headers and their payloads are matched against specific predefined rules/strings to see if they contain a malicious content. Snort can run in two modes:
- Packet Sniffing
- This mode have no special use, all you can do is just look at the traffic coming at the interface.
- Network Intrusion detection
- This mode is the actual use of snort, in this mode snort monitor the traffic and block any unwanted traffic using the rules.
Installing snort from source is a bit tricky, let see how we can install snort intrusion detection system on Ubuntu from its source code.
Step 1: Prepare to install
Before actually installing snort, their are some of its per-requisites, you can run following commands to install all the required per-requisites.
sudo apt-get update sudo apt-get dist-upgrade
Reboot after running the above commands.
sudo apt-get install build-essential sudo apt-get install -y libpcap-dev libpcre3-dev libdumbnet-dev sudo apt-get install -y zlib1g-dev liblzma-dev openssl libssl-dev sudo apt-get bison flex
After running these commands you are ready to install snort.
Step 2: Install Daq
Next step is to install daq (snort require daq to run), daq source code is available on their site for download.
You can create a separate folder for all your downloads mkdir ~/snort (Just to keep all downloads at one place), you need to download and extract daq.
cd ~/snort wget https://www.snort.org/downloads/snort/daq-2.0.6.tar.gz tar -xvzf daq-2.0.6.tar.gz cd daq-2.0.6 ./configure make sudo make install
Commands above will download the daq source code and then install it.
Step 3: Install Snort
You are now ready to download snort source code.
cd ~/snort wget https://www.snort.org/downloads/snort/snort-2.9.8.3.tar.gz tar -xvzf snort-2.9.8.3.tar.gz cd snort-2.9.8.3 ./configure make sudo make install sudo ldconfig sudo ln -s /usr/local/bin/snort /usr/sbin/snort
Snort is now installed on your system, but you need to configure snort to make use of it. To make sure snort is installed on your system, run snort -V , if you see the following output, then you are on right track.
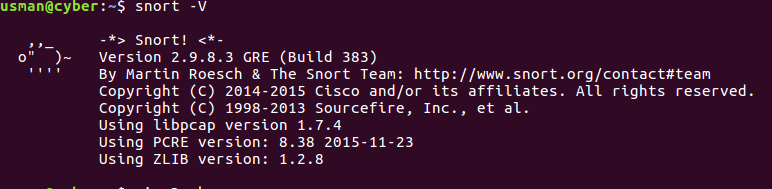
Step 4: Create some required directories
Snort need some folder and files to place its logs,errors and rules files, you can create a bash script and run these commands at once or you can just execute them one by one.
sudo groupadd snort sudo useradd snort -r -s /sbin/nologin -c SNORT_IDS -g snort sudo mkdir /etc/snort sudo mkdir /etc/snort/rules sudo mkdir /etc/snort/rules/iplists sudo mkdir /etc/snort/preproc_rules sudo mkdir /usr/local/lib/snort_dynamicrules sudo mkdir /etc/snort/so_rules sudo touch /etc/snort/rules/iplists/black_list.rules sudo touch /etc/snort/rules/iplists/white_list.rules sudo touch /etc/snort/rules/local.rules sudo touch /etc/snort/sid-msg.map sudo mkdir /var/log/snort sudo mkdir /var/log/snort/archived_logs sudo chmod -R 5775 /etc/snort sudo chmod -R 5775 /var/log/snort sudo chmod -R 5775 /var/log/snort/archived_logs sudo chmod -R 5775 /etc/snort/so_rules sudo chmod -R 5775 /usr/local/lib/snort_dynamicrules sudo chown -R snort:snort /etc/snort sudo chown -R snort:snort /var/log/snort sudo chown -R snort:snort /usr/local/lib/snort_dynamicrules cd ~/snort/snort-2.9.8.3/etc/ sudo cp *.conf* /etc/snort sudo cp *.map /etc/snort sudo cp *.dtd /etc/snort cd ~/snort/snort-2.9.8.3/src/dynamic-preprocessors/build/usr/local/lib/snort_dynamicpreprocessor/ sudo cp * /usr/local/lib/snort_dynamicpreprocessor/
Please do not ignore these commands.
Step 6: Editing snort configuration files
We need to modify some configuration files to run snort in network intrusion detection mode, first comment out all the rules in snort configuration file using
sudo sed -i "s/include \$RULE\_PATH/#include \$RULE\_PATH/" /etc/snort/snort.conf
Find your network details using ifconfig
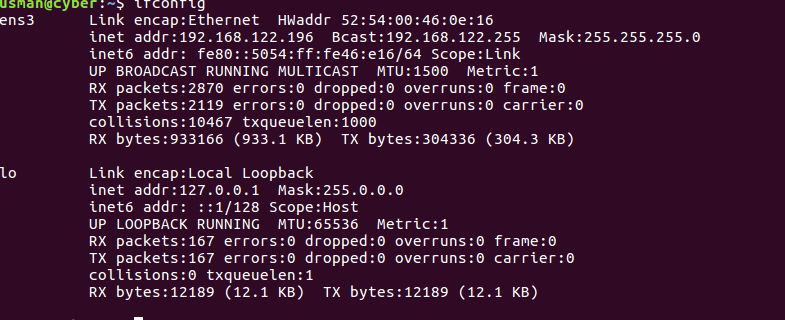
Here “ens” is the interface I am capturing traffic on, my mask is 255.255.255.0, so my network is : 192.168.122.0/24
You need to find this details to put in snort.conf file.
sudo vi +45 /etc/snort/snort.conf
This command will open the snort.conf file and move you to 45th line, make sure your following line look like this
ipvar HOME_NET 192.168.122.0/24
The underlined part should be your network details. (Adjust appropriately).
#open file and move to line 104 sudo vi +104 /etc/snort/snort.conf
Following the line at 104, make sure your paths look like this.
var RULE_PATH /etc/snort/rules
var SO_RULE_PATH /etc/snort/so_rules
var PREPROC_RULE_PATH /etc/snort/preproc_rules
var WHITE_LIST_PATH /etc/snort/rules/iplists
var BLACK_LIST_PATH /etc/snort/rules/iplists
#open file and move to line 545 sudo vi +545 /etc/snort/snort.conf
UN-comment the 545th line and make it look like this
include $RULE_PATH/local.rules
Step 7: Test Snort
As a final step we need to make sure that snort is running in network intrusion detection mode, for that we need to insert a rule in our “/etc/snort/rules/local.rules” file.
Open this file and paste the following rule
alert ip any any -> any any (msg:"ATTACK RESPONSES id check returned root"; content: "uid=0(root)"; classtype:bad-unknown; sid:498; rev:3;)
Now run snort using
sudo snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i ens3
Note : It will start listening on interface ens3, make sure you replace it with your interface name. After running snort, open another ssh connection to the server and run this command:
ping -b 255.255.255.255 -p "7569643d3028726f6f74290a" -c3
You should now be able to see alerts on ssh where you have started snort, it should look something like this:
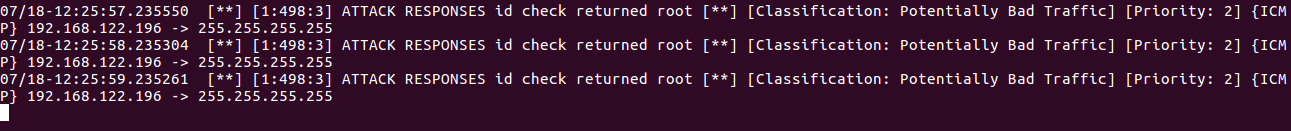
Hi,
Your rule is giving me the following error:
ERROR: /etc/snort/rules/local.rules(1) Rule options must be enclosed in ‘(‘ and ‘)’.
Thanks.
Hey Guys,
I am trying to dowload
wget https://www.snort.org/downloads/snort/daq-2.0.6.tar.gz
But getting the error below –
system@ubuntu:~$ wget https://www.snort.org/downloads/snort/daq-2.0.6.tar.gz
–2020-05-21 05:31:22– https://www.snort.org/downloads/snort/daq-2.0.6.tar.gz
Resolving http://www.snort.org (www.snort.org)… 104.18.138.9, 104.18.139.9, 2606:4700::6812:8b09, …
Connecting to http://www.snort.org (www.snort.org)|104.18.138.9|:443… connected.
HTTP request sent, awaiting response… 404 Not Found
2020-05-21 05:31:22 ERROR 404: Not Found.
Any clue for fixes