WordPress Security Through Logging & Audit Trail
WordPress security; many typically think of hardening techniques, WordPress hacks, firewalls and other similar defensive mechanisms and plugins. Though there is another very important aspect of security; logging and audit trials.
A WordPress audit trail allows you to keep an eye on the production of all your users, keep a record of every change that happens on your WordPress, and identify possible malicious attacks against your WordPress website before they actually happens. This article explains how to use the WP Security Audit Log plugin to keep an eye on your WordPress and WordPress multisites, and catch hackers red handed before they actually damage your website.
Introduction to WP Security Audit Log
First things first, let’s introduce the plugin. The WP Security Audit Log is a very easy to use WordPress plugin. Once installed it automatically starts keeping a record of all the changes that are happening on your WordPress in a security audit trail, as explained in this short video.
You can enable or disable the monitoring of specific WordPress changes from the Enable/Disable Alerts section.
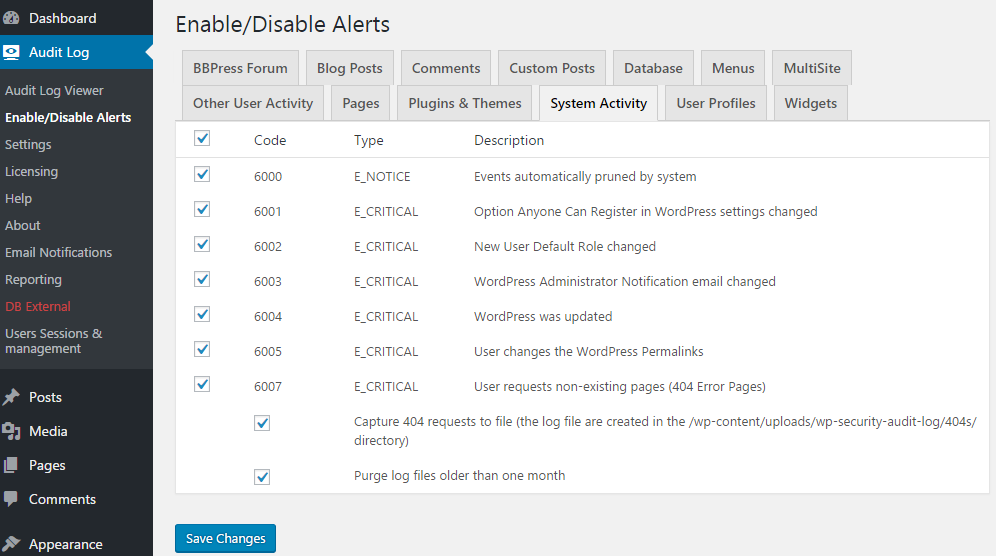
Security Tip: From a security point of view, the more information you have in the logs the better, so we do not recommend you to disable any of the alerts.
Now that you have the plugin installed, let’s look into how you can make better use of the WordPress audit logs.
Identify WordPress Hack Attacks Before They Happen
First we have to understand how malicious hackers work and what they do when they hack into a WordPress website to know what to look for. So below are some examples of what you should keep an eye on to identify the most common WordPress hack attacks.
Failed WordPress Logins
Starting with the basics, the most common attack against WordPress is a password brute force attack. So in the audit log you should look for Alert 1003 as per the screenshot below.
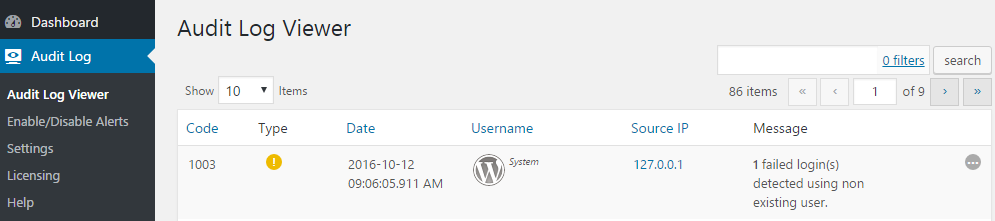
Alert code 1003 means that someone is trying to login to your WordPress website using a non-existing username. Not much to worry about, unless it is happening frequently and from the same IP address. You should worry if you see a lot of Alerts with code 1002, which are failed logins for an existing username.
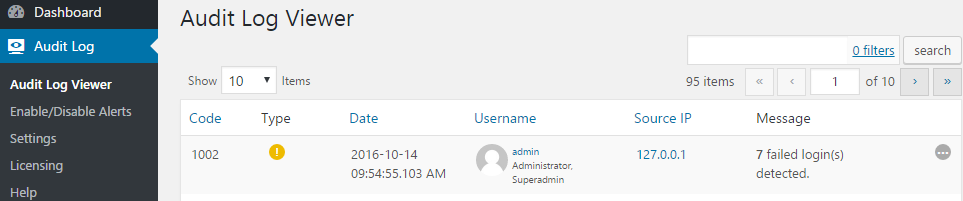
If you see a lot of 1002 Alerts, and the failed login attempts are not from the account owner then the attackers have guessed the username. Again, not much to worry about as long as the username has a strong password, but definitely something to keep an eye on.
Tip: Use the All Add-Ons package for WP Security Audit Log to add the Search, Reporting and other functionality.
Automated WordPress Security Scans
Another common sign that your WordPress is under attack is when an IP address is requesting a lot of non-existing pages (404 errors). This happens because attackers typically use automated scanners (such as WPScan WordPress black box scanner) to send bogus requests to your WordPress, with the aim of identifying a vulnerability or security hole they can exploit to break into your website.
Note that it is normal to have a few requests to non-existing pages, so if you see Alert code 6007 in your WordPress audit trial there is no need to panic. The problem is when there are many of such requests. Start worrying about it if the same IP address, or a number of IP addresses are requesting a lot of non-existing pages at the same time, as seen in the below screenshot.
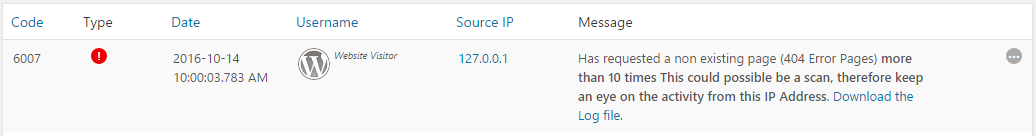
The WP Security Audit Log plugin keeps a log of the requests to non-existing pages (404 requests), so if you are suspicious about something, download the log file (link available in the alert as seen in the above screenshot) and analyse it. Below is an extract from a log file which was generated when someone was trying to enumerate users on a WordPress website. Notice the patterns in the requests, definitely a sign of someone using a fuzzer.
Attempts: 1 – Request URL: www.local.com/?author=1
Attempts: 2 – Request URL: www.local.com/?author=2
Attempts: 3 – Request URL: www.local.com/?author=3
Attempts: 4 – Request URL: www.local.com/?author=4
Attempts: 5 – Request URL: www.local.com/?author=5
Attempts: 6 – Request URL: www.local.com/?author=6
Attempts: 7 – Request URL: www.local.com/?author=7
Attempts: 8 – Request URL: www.local.com/?author=8
Attempts: 9 – Request URL: www.local.com/?author=9
Attempts: 10 – Request URL: www.local.com/?author=10
Attempts: 11 – Request URL: www.local.com/?author=11
Attempts: 12 – Request URL: www.local.com/?author=12
Attempts: 13 – Request URL: www.local.com/?author=13
Attempts: 14 – Request URL: www.local.com/?author=14
Attempts: 15 – Request URL: www.local.com/?author=15
Attempts: 16 – Request URL: www.local.com/?author=16
Attempts: 17 – Request URL: www.local.com/?author=17
Attempts: 18 – Request URL: www.local.com/?author=18
Attempts: 19 – Request URL: www.local.com/?author=19
Attempts: 20 – Request URL: www.local.com/?author=20
Attempts: 21 – Request URL: www.local.com/author/admin/
Attempts: 22 – Request URL: www.local.com/author/sysadmin/
Attempts: 23 – Request URL: www.local.com/author/wordpressadmin/
Attempts: 24 – Request URL: www.local.com/author/website/
Attempts: 25 – Request URL: www.local.com/author/user1/
Attempts: 26 – Request URL: www.local.com/author/robert/
Attempts: 27 – Request URL: www.local.com/author/administrator/
Attempts: 28 – Request URL: www.local.com/author/wordpress/
Attempts: 29 – Request URL: www.local.com/author/wpadmin/
Attempts: 30 – Request URL: www.local.com/author/root/
Keep an Eye on Your WordPress User Accounts
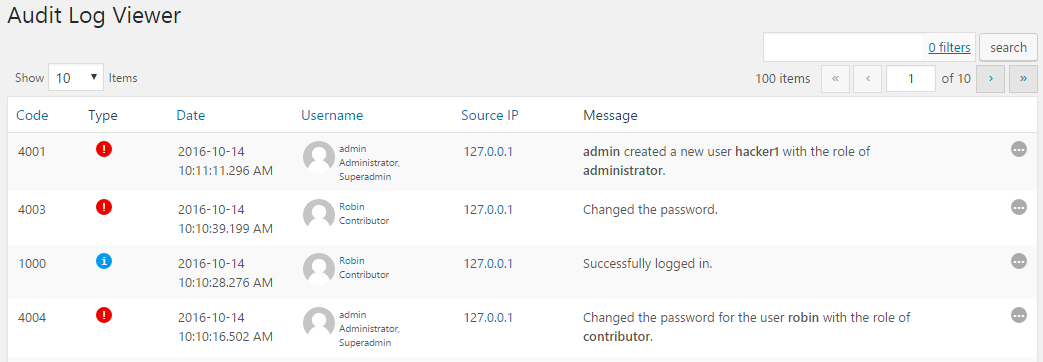
If attackers find and exploit a security hole in your WordPress, most probably they will change the password of a username or create a new username to retain access to your WordPress. And since many WordPress administrators rarely access the users’ page in the WordPress dashboard malicious hackers typically manage to retain access to the hacked WordPress site for years.
If you use WP Security Audit Log to keep a WordPress audit trail you will have a record of all this; when a WordPress user’s password is changed, when a new user is created etc, as seen in the below screenshot.
Get Alerted Instantly Via Email of Attacks – Prevent WordPress Hacks
The WordPress audit trail is definitely handy, but no one has the time to browse through it every hour to see what is happening. That is why WP Security Audit also has the Email Notifications Add-On, so you can be alerted instantly via email when important changes happen on your WordPress.
You can even configure the plugin to send you an email the first time a user logs in. Therefore if the attackers exploited a SQL Injection and created the WordPress user directly in the database, the first time they login with that WordPress user you will be alerted via email and catch them red handed.
Other WordPress Audit Trail Tools to Prevent WordPress Attacks and Keep Everything Under Control
The WP Security Audit Log plugin has several other add-ons available such as Search, Reports, External Database support and Users Sessions Management. All of these add-ons bundled together make it easier for you to keep track of what is happening on your WordPress, identify potential harmful attacks before they happen, catch hackers red handed before they do any damage, and in the unfortunate case of a successful hack attack, do all the forensics needed to find out what exactly happened and close the security hole.